In today’s digital age, cybersecurity education is crucial for protecting sensitive information and systems. Hiring a competent cybersecurity instructor is vital for equipping students or employees with the necessary skills to defend against cyber threats.
When searching for a cybersecurity instructor, it is crucial to look beyond technical expertise and seek out someone with real-world experience. Look for candidates who have worked in the field and have practical knowledge of current cyber threats and how to mitigate them effectively. Experience trumps theoretical knowledge in this fast-paced and ever-evolving industry.
Additionally, consider individuals who possess strong communication skills as they will need to effectively convey complex security concepts to learners of varying backgrounds. A good cybersecurity instructor should be able to engage students through interactive learning activities, case studies, and real-world simulations. Remember, the goal is not just to teach theory but also to inspire students to develop critical thinking skills and proactive cybersecurity practices that can be applied in a professional setting.
This guide will help you define the role, outline the required skills, provide sample interview questions, and describe the ideal candidate profile for a cybersecurity instructor.
Defining the Role
Cybersecurity Instructor
A cybersecurity instructor is responsible for teaching and training individuals in various aspects of cybersecurity. This role involves developing curriculum, delivering lectures, conducting practical labs, and assessing the knowledge and skills of students or employees. The instructor must stay updated with the latest cybersecurity trends, tools, and best practices to provide relevant and up-to-date education.
Key Responsibilities
– Curriculum Development: Design and update cybersecurity courses, including theoretical and practical components.
– Instruction: Deliver engaging lectures, workshops, and hands-on labs to students or employees.
– Assessment: Create and grade exams, quizzes, and practical assignments to evaluate learners’ progress.
– Mentorship: Provide guidance and support to students or employees, helping them understand complex concepts and develop their skills.
– Staying Current: Continuously update personal knowledge and teaching materials to reflect the latest developments in cybersecurity.
– Collaboration: Work with other instructors, industry experts, and stakeholders to ensure comprehensive and cohesive cybersecurity education.
Skills Required
Technical Skills
– Knowledge of Cybersecurity Principles: In-depth understanding of cybersecurity concepts, including network security, cryptography, threat analysis, and risk management.
– Hands-on Experience: Practical experience with cybersecurity tools and technologies such as firewalls, intrusion detection systems, SIEM, and encryption software.
– Programming Skills: Proficiency in programming languages like Python, Java, or C++ for developing and analyzing security tools and scripts.
– Certifications: Relevant certifications such as CISSP, CEH, CompTIA Security+, and Certified Information Security Manager (CISM).
Educational Skills
– Curriculum Development: Ability to design comprehensive and engaging courses that cover both theoretical and practical aspects of cybersecurity.
– Teaching Experience: Previous experience in teaching or training, with the ability to explain complex concepts in an understandable manner.
– Assessment Design: Skills in creating and grading assessments to measure learners’ understanding and progress.
Soft Skills
– Communication: Excellent verbal and written communication skills to effectively deliver lectures and provide feedback.
– Patience: Patience and understanding to support learners of varying skill levels.
– Adaptability: Ability to adapt teaching methods to different learning styles and keep up with evolving cybersecurity trends.
– Problem-Solving: Strong problem-solving skills to help students or employees tackle cybersecurity challenges.
Sample Interview Questions
Technical Questions
- Can you explain the difference between symmetric and asymmetric encryption?
– Ideal Answer: Symmetric encryption uses the same key for both encryption and decryption, making it faster but requiring secure key management. Asymmetric encryption uses a pair of keys (public and private) for encryption and decryption, enhancing security for key exchange processes.
- How would you secure a network against a potential ransomware attack?
– Ideal Answer: To secure a network against ransomware, I would implement robust backup solutions, ensure regular software updates, use advanced antivirus and anti-malware tools, restrict user permissions, and educate users on recognizing phishing attempts.
- What are the key steps in a risk assessment process?
– Ideal Answer: The key steps in a risk assessment process include identifying assets, identifying potential threats, assessing vulnerabilities, evaluating the impact of potential threats, and prioritizing risks based on their severity.
Educational Questions
- How do you stay updated with the latest trends and developments in cybersecurity?
– Ideal Answer: I stay updated by regularly attending industry conferences, participating in webinars, following cybersecurity blogs and news sites, and engaging in continuous learning through certifications and online courses.
- Can you provide an example of a hands-on lab activity you’ve designed for students?
– Ideal Answer: One example is a lab where students simulate a phishing attack to understand how attackers operate and then create email filters and security policies to prevent such attacks. This hands-on experience helps students grasp practical cybersecurity measures.
- How do you handle students who are struggling to grasp complex cybersecurity concepts?
– Ideal Answer: I offer additional support through one-on-one tutoring sessions, provide supplementary resources, use different teaching methods to cater to various learning styles, and encourage peer learning and group discussions to facilitate better understanding.
Behavioral Questions
- Describe a time when you had to adapt your teaching style to accommodate different learning styles in your classroom.
– Ideal Answer: I once had a class with diverse learning preferences. To accommodate everyone, I incorporated a mix of lectures, hands-on activities, visual aids, and group projects. I also provided online resources and encouraged interactive discussions to ensure all students could engage with the material.
- How do you handle feedback from students or employees about your teaching methods?
– Ideal Answer: I value feedback as it helps me improve. I actively seek input from students, conduct anonymous surveys, and have open office hours for direct feedback. I then reflect on this feedback and make necessary adjustments to my teaching methods and materials.
- What motivates you to work in the field of cybersecurity education?
– Ideal Answer: I am passionate about cybersecurity and believe in the importance of educating the next generation of professionals to protect against evolving cyber threats. The challenge of staying current in a dynamic field and the opportunity to inspire and equip learners with critical skills motivates me every day.
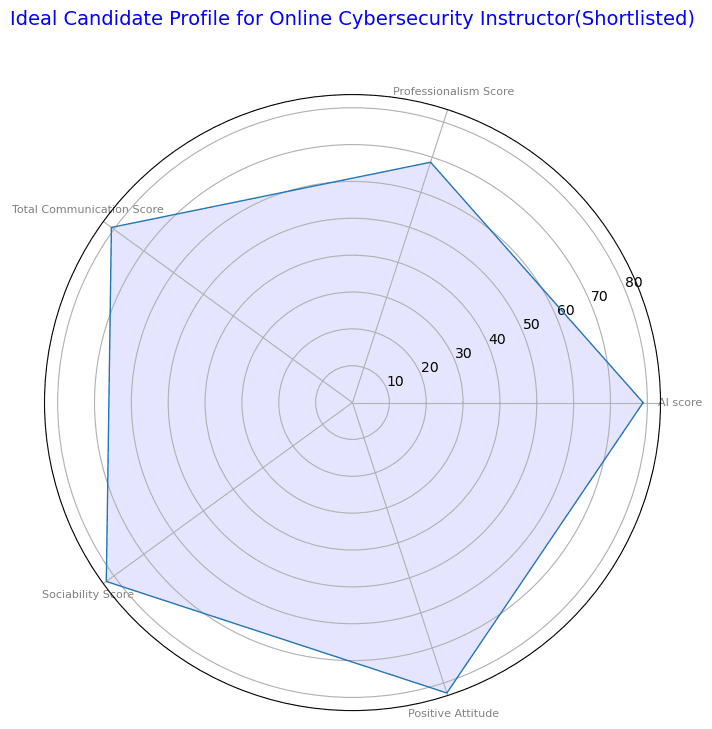
Ideal Candidate Profile
Educational Background
– Degree: A degree in Computer Science, Information Security, or a related field.
– Certifications: Relevant certifications such as CISSP, CEH, CompTIA Security+, and Certified Information Security Manager (CISM).
Professional Experience
– Industry Experience: Several years of hands-on experience in the cybersecurity field, working with various security technologies and frameworks.
– Teaching Experience: Proven track record of teaching or training in cybersecurity, with the ability to explain complex concepts clearly and effectively.
Technical Skills
– Cybersecurity Knowledge: Deep understanding of cybersecurity principles, including network security, cryptography, threat analysis, incident response, and risk management.
– Practical Skills: Hands-on experience with security tools and technologies such as firewalls, intrusion detection systems, Security Information and Event Management (SIEM), and encryption software.
– Programming Skills: Proficiency in programming languages relevant to cybersecurity, such as Python, Java, or C++.
Educational Skills
– Curriculum Development: Ability to design comprehensive and engaging courses that cover both theoretical and practical aspects of cybersecurity.
– Assessment Design: Skills in creating and grading assessments to measure learners’ understanding and progress.
Soft Skills
– Communication: Excellent verbal and written communication skills to effectively deliver lectures and provide feedback.
– Patience: Patience and understanding to support learners of varying skill levels.
– Adaptability: Ability to adapt teaching methods to different learning styles and keep up with evolving cybersecurity trends.
– Problem-Solving: Strong problem-solving skills to help students or employees tackle cybersecurity challenges.
Conclusion
Hiring a cybersecurity instructor is a critical step in ensuring that your organization or educational institution can effectively educate and train individuals in the essential field of cybersecurity. By defining the role clearly, identifying the required skills, asking the right interview questions, and understanding the ideal candidate profile, you can find a qualified and passionate instructor who will inspire and equip learners to tackle cybersecurity challenges head-on. Stay proactive in your recruitment efforts and continuously refine your hiring process to attract the best talent in cybersecurity education.
Also read:
Introduction to the Series: The Hiring Guide Using AI Interviews
Hiring Guide Blog Series: How to hire an AI Engineer
Hiring Guide: How to hire a Data Scientist
Hiring Guide: How to hire a Technical Content Writer
Hiring Guide: How to hire a Software Engineer
Hiring Guide: How to hire a Technical Recruiter
Interviewer.AI is a technology platform purposely built to support Recruiters and HR teams in finding top talent for their companies. We also work with universities to help them with admissions and coaching, helping them use technology to solve for talent and training. Our mission is to make hiring equitable, explainable, and efficient. to screen in advance and shortlist the candidates that meet the criteria set.
Schedule a demo today to learn more about how AI interviews can help your hiring.
Gabrielle Martinsson is a Content Writer at Interviewer.AI. She’s a tech geek and loves optimizing business processes with the aid of tech tools. She also loves travelling and listening to music in her leisure.